Information security plan
The purpose of process of information security plan is establishment method to protect the information of company’s confidentiality.
Process of information security plan is motive is secure the information of company in the soft & hard formats, the purpose of the procedure is to draw methods & defense system that theft of the confidential data can safe, this information can be in form of personal information, supplier records, customer listing and prices, contractors information, employees records etc, protection against any anticipated threats / bugs and viruses, hackers attempts that can categorized as hazards for the information system. The security and integrity of such information and to protect against unauthorized access of the pages, data, information to or use of such collection of data in a manner that raises a significant menace of characteristics stealing or scam. The information of the company is achieved methods, documents, system etc, after the long practices, experiments & expense as results unique informative system is established that should be proper secure is very important for the company confidentiality & respective information, documents.
This process is unique information safety & security against stealing of information by unauthorized objects that this process applicable to all documents, records, research documents, standards, personal information etc, which leakage can harm the company as well as individual loss. Company should take care those information should not be available, accessible for the public domain. The scope of information security plan is applied as company terms and policy.
Information security plan is established & implementation responsibilities of information technology peoples, system administrator is conducting the information from the various department & listing information for the establish unique system for the security if the information is in soft form, in case of the hard copies information, document is with company that company is decided for the security along with soft formats. The information security is the responsibility of the company’s all working staff & peoples are working at the location, implementation of the procedures in all their activities. Generally system administrator is responsible for maintaining a information security, all the master lists are established, maintain & updated by system administrator that all the concern duties & responsibilities are defined as requirements.
Security Program
Security program is established for the identification of the information and classification, identification of the risk and systematic records & security of the each document is primary objective of the program. Influence management, guidelines, database management for the security helps to improvement in program, restriction entry in document storage room, workplace & access information of regular practices.
- Design of the information security program is established by the system administrator with support of the quality manager that all the required implementation factors, maintain appropriate security measures.
- Classification of information of the company is very important that which document is needs categorized security to prevent theft, unauthorized access. All the information shall be controlled and only the employee who is authorized by the management.
- Identification of risk is very important, identified and assessed any internal or external risks should be proper classified, all the information of each accesses should storage to easier for identify.
- Company should evaluate & continual improvement by inspecting effectiveness of the procedures, documents and system.
- Each access keys should be permission for accessing are reasonable, completion of the information, accessing codes, keys and passwords should be limited for each user.
Individual Permission Assignment
Employee individual permission assignment is for classified serious data which is required for reasonable access, each documents, records and information which is maintained as secured should be need to individual permission for accessing by assignment, employee information collection and assignment of the permission is fully controlled over the information technology team. Employee information is completed by human resources department executive by on request of employee individually, all the employee requests are maintain by human resource department, hence information technology division is received the request and on base of the approvals of the concern peoples user identification number and password is allocated to employee for the accessing information, Here as below given example of the permission assignment form which is passed by human resource department and information technology department is completed further requirements:
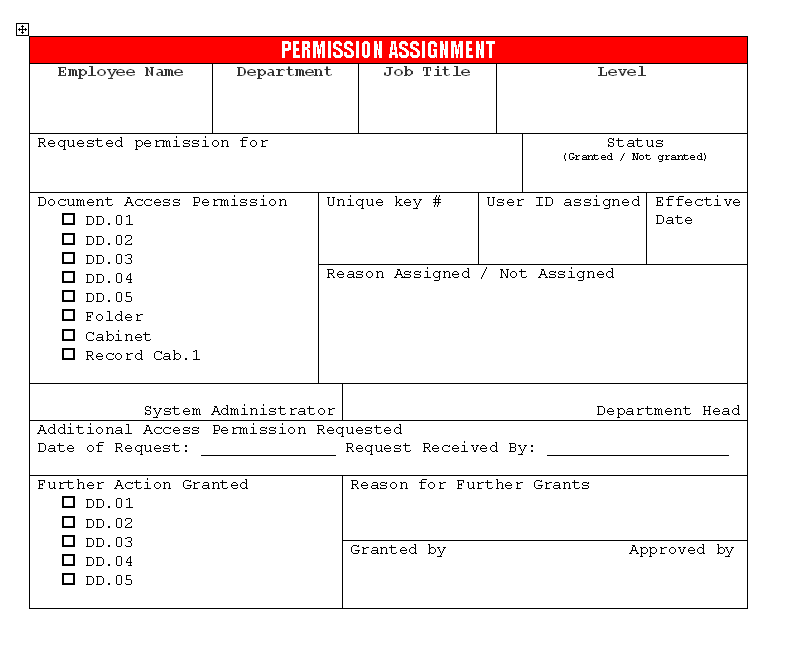
Whenever the permission assignment form is submitted by the employee that employee should be agree the terms of the permission, accessing information of company, on agreement of the employee for not misuse of information. Human resource department provided the understanding of agreement to employee for the read & review to understand policy of permission assignment.
Monitoring on access
Company should have to proper system to monitoring on activities of the employee data and also need to define and conduct the audit for the security system of the company for the information and technology to ensure the system is proper conducting the information, all the function is working properly with employee is used fairly by the system.
———————————————————————–
Download Individual permission Assignment form
———————————————————————–